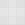
Failed to retrieve Realm for the Invalid Domain : school.edu
Ellucian Ethos Identity Server (EEIS) is basically a WSO2 Identity Server with addons, particularly a CAS module for adding the CAS sso protocol to WSO2’s already impressive list of supported protocols. Below I will describe a particular error with this setup experienced when EEIS is federated. My particular issue came up when this was configured with Azure Active Directory (AAD) as the upstream federation server, but it looks as if the problem would probably present itself when using other common services under similar conditions.
Basically the problem lies in the multi-tenant code in the CAS module. It seems to assume that the userPrincipalName (typically Email Address but it could be another type of “scoped” credential that may not be external email address) is actually interpreting “user1@school.edu” as “user1” in “school.edu a tenant domain realm” in WSO2 multi-tenant handling instead of user1@school.edu as a singular username. This fails for most schools because their structure doesn’t require them to use anything other than the master tenant.
This behavior can simply be alleviated by sending down a “non-scoped” username. If you’re using AAD it’s probably because you’re using Active Directory on-premises and can use any of the synced ldap attributes like user.onpremisessamaccountname (sAMAccountName – the login for Active Directory). Then send userPrincipalName (and emailAddress) as separate SAML2 claims that EEIS can then bring in as normal claims. Remember, normal WSO2 Identity Server service providers allows you to switch the subject identifier for each service provider, as long as it is among the custom claims you send to the service.
<insert screenshots of microsoft – azure active directory – enterprise application – single sign on – saml2 – claims – name id claim>
<insert screenshot of wso2 – identity server – identity provider – saml2 identity server – claims>